THM{Zero Logon} Walkthrough

Summary
This room is a beginner-friendly way to start understanding how attackers exploit vulnerabilities in general and the ZeroLogon vulnerability specifically.
Note: This room contains updated commands for the AttackBox to install the impacket virtual environment.
The Zero Day Angle
Read through this section and study the links given. This will help with understanding the basics of RPC, which is fundamental to this room and exploit.
Impacket Installation
As stated in the walkthrough, Impacket can be quite fussy, so it is recommended that you use the Attack Box for this module. However, if you are going to use the Attack Box, you will need to update the commands you're using to install and run the Python virtual environment. Since this room was released, there have been several updates to Python, and Python3 now fails to launch Impacket. The THM team has been notified, and I'll update this blog if the situation changes, but take a look at the instructions.
The command instructions in the room are as follows:
python3 -m pip install virtualenv
python3 -m virtualenv impacketEnv
source impacketEnv/bin/activate
pip install git+https://github.com/SecureAuthCorp/impacket
The issue here is that when running these commands in the Attack Box you get the following error:
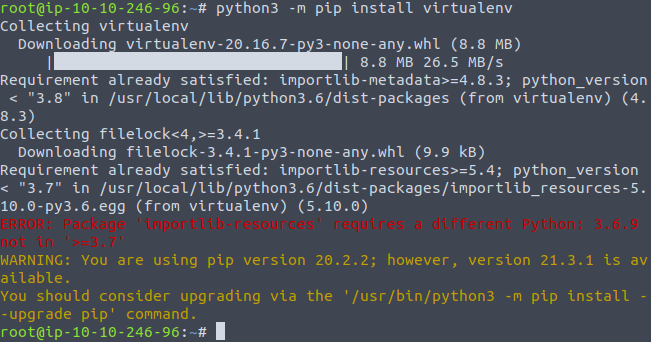
As you can see above, the first command will run partially and then throw a single failure. If you, like me try to move forward thinking, "it's only one error", you will find yourself trying to run the second command which the box doesn't recognize because of the error in the previous command.
To fix this error, we need to update the version of Python we are running. Your updated command should be the following:
python3.9 -m pip install virtualenv
python3.9 -m virtualenv impacketEnv
source impacketEnv/bin/activate
pip install git+https://github.com/SecureAuthCorp/impacket
Notice all we are doing is changing the version of python we are running which is simple but has taken me the last two days to figure out, so I figured I'd share it here to help anyone who follows to save a day or two.
After executing these commands, you will be moved to the Python 3.9 virtual envirionment which will allow us to exploit Zero Logon.
Note: If you already attempted to run impacket with python3 and are trying to pivot to 3.9, I recommend you terminate and start a new Attack Box, because whether you pivot to 3.9 or not, having run python3 on the machine in the past seems to make the issue persistent even if you re-run the command with the updated version. I'm sure given enough time, you could find a fix for this, but it is much easier if you just swallow your pride and reboot the machine. Once rebooted, begin with the updated commands and you shouldn't have a problem.
The Proof of Concept
The instructions in this section are very extensive. If this is your first time seeing something like this, you may need to read through it a couple of times to get a good understanding of what is going on here.
Once you understand the instructions, you can go as hardcore as you want. You can write the new code from scratch, paste in the code as the end of the instructions, or just wget the code with the url at the end of the instructions.
Try the first two ways and if you must, use wget. The format will look like this wget [https://raw.git...].
Questions
Q: What method will allow us to chang passwords over NRPC?
A: There is a method linked at the beginning of the task 3 instruction sheet that has also been mentioned previously in this room.
Q: What are the required fields for the method per the Microsoft Documentation?
A: Identify the fields in that same link you found for the first answer.
Q: What Opnumber is the Method?
A: This is clearly identified in the same MSFT method documentation.
Q: Modify the PoC
A: Get your code working so that we can use it to exploit the box in the next task.
Lab It Up!
Now that we've had some pretty extensive reading into RPC, Impacket, and the PoC exploit code, lets exploit a vulnerable Domain Controller.
First we're going to run Nmap to get some basic information about the DC that we will need to run the exploit.
I'm going to run something like:
nmap -sV -sC [IP]
Note:
nmap -sV = version enumeration
nmap -sC = common scripts
When running the exploit in this section, remember to continue using python3.9. When running python3 with the exploit, I get an error saying that impacket has no 'NetrServerPasswordSet2' module. However, when running this with python3.9, the password is cracked and changed usually within a couple seconds.
Now that we have the exploit code written, assuming it is written correctly, the hard part of this room is over. Pass the code to the DC by using this command: python3.9 [name of exploit file] [NetBIOS name of DC] [IP]
You should see output similar to the following:
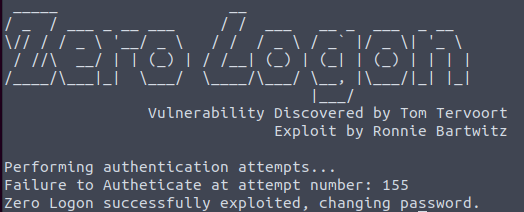
Now that you've gotten a password cracked, lets check out what other passwords this box has on it using secrets.py. After running all your impact commands, you'll notice that you have an impacketEnv directory in ~. To find secrets.py, lets navigate to ~/impacketEnv/bin and then copy secrets.py back to our original working directory. Then we can return to that directory as well. Now we are back in ~ in the impacket environment, and we have access to secrets.py.
To see the hashes on the machine, run secretsdump.py -just-dc -no-pass [NetBios name]\$@[IP]. We can now see a whole bunch of hashes on the machine.
Now that you have the hash, we are going to use winrm to gain access to the machine. Run the command evil-winrm -u [user account] -H [user's hash] -i [IP]. Assuming you've gathered the correct informaiton and formatted it correctly, you will have access to the machine's command line.
Now that you have access to the machine's command line, dig around in the file system, opening any intersting file you find, and you will find the flag.
Questions
Q: What is the NetBIOS name of the Domain Controller?
A: If you ran the Nmap correctly, the NetBIOS name should be explicitly listed in the output.
Q: What is the NetBIOS domain name of the network?
A: Note here that this is just the domain name and not the FQDN
Q: What domain are you attacking?
A: This contains the domain name from the last question.
Q: What is the Local Administrator's NTLM hash?
A: Check for the common name of a windows local administrator in the list of dumped credential, and the second half of that user's dump will be their NTLM hash.
Q: How many domain admin accounts are there?
A: The prefix "a-" is typically indicitive of a domain admin accounts.
Q: What is the root flag?
A: Dig around in the machine's file system to find the file.
Congratulations! You've come to the end of the room. I hope this helped make your learning experience more streamlined.
